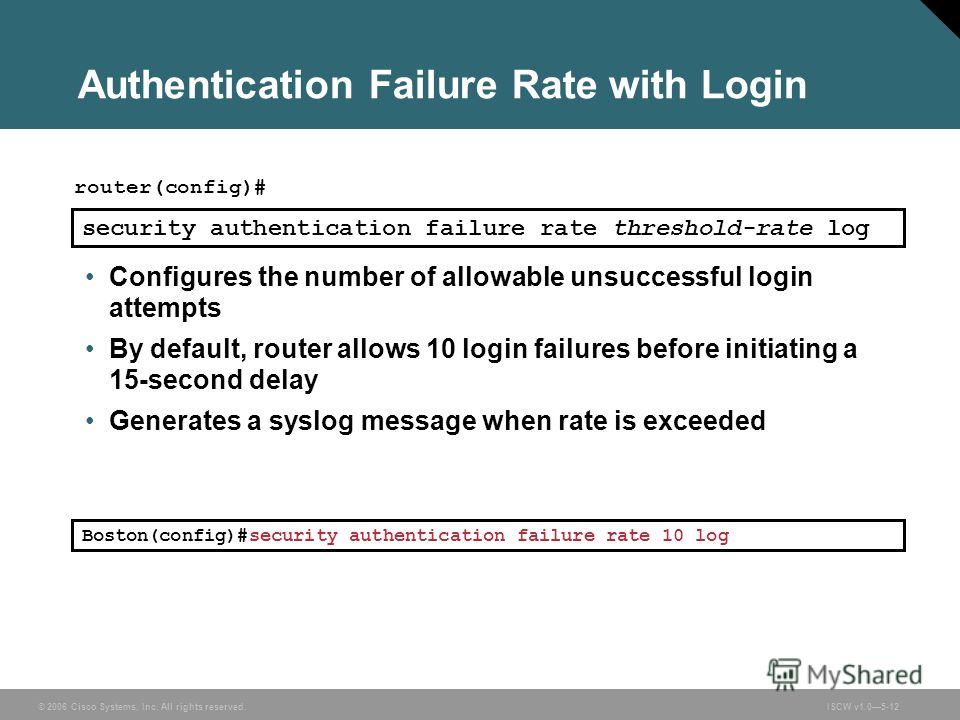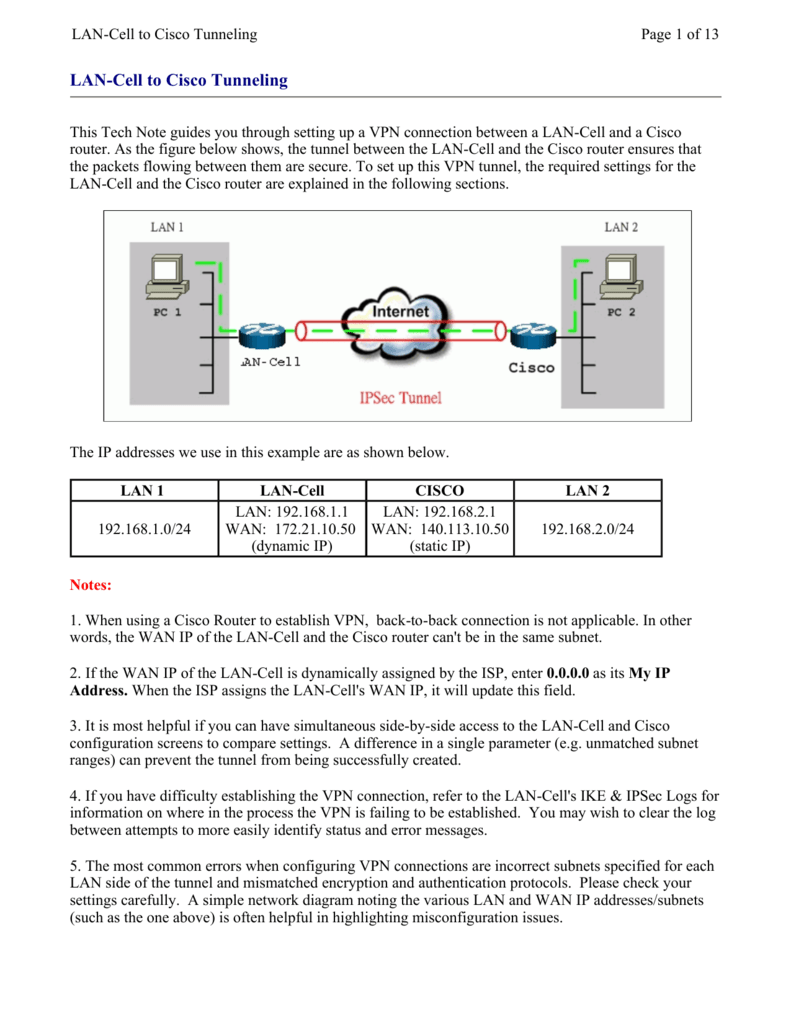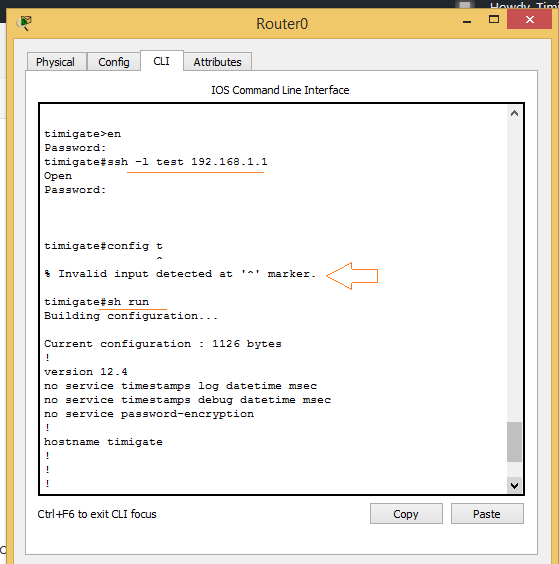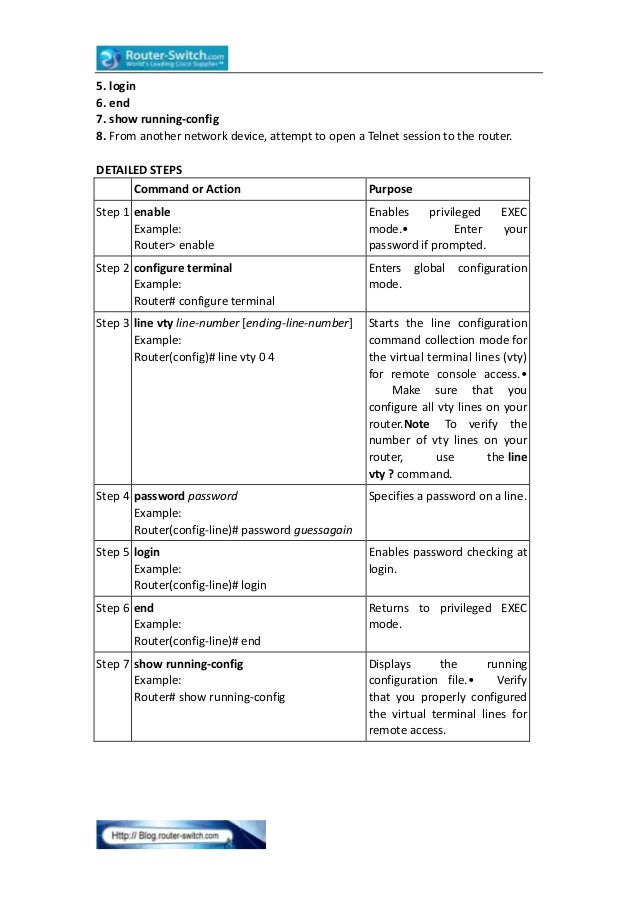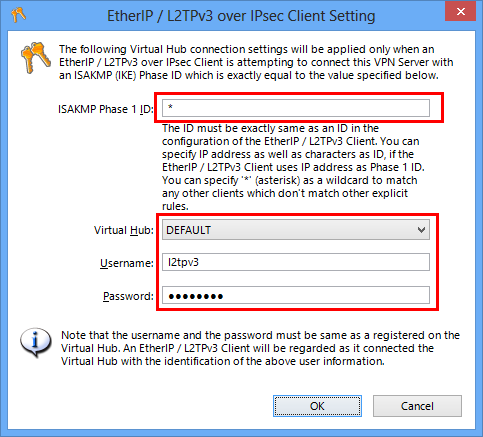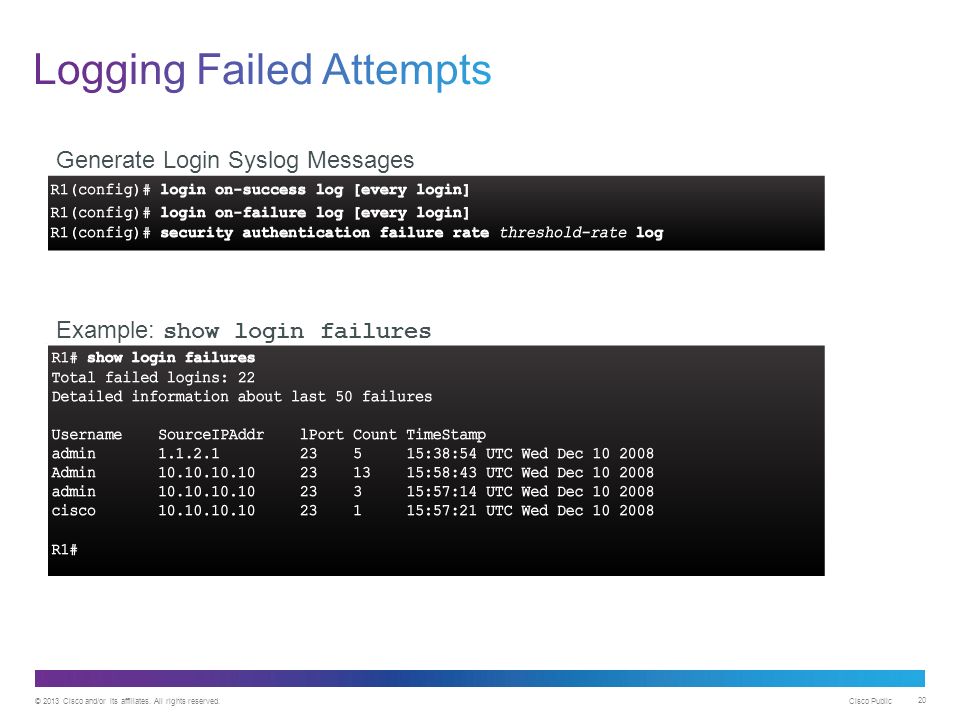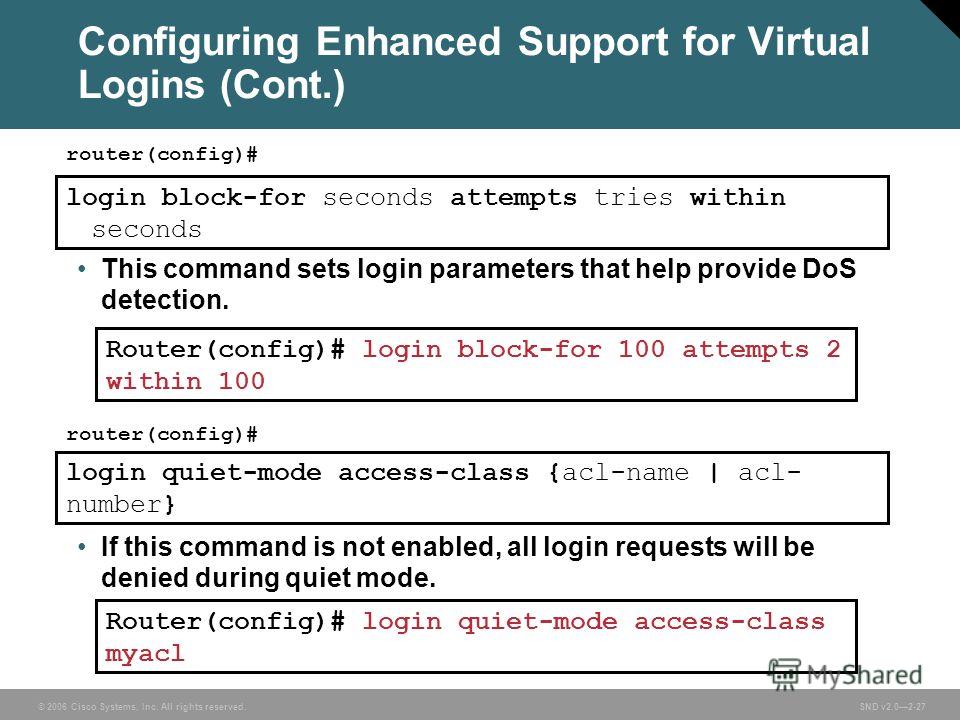
Презентация на тему: "© 2006 Cisco Systems, Inc. All rights reserved. SND v Securing the Perimeter Securing Administrative Access to Cisco Routers.". Скачать бесплатно и без регистрации.
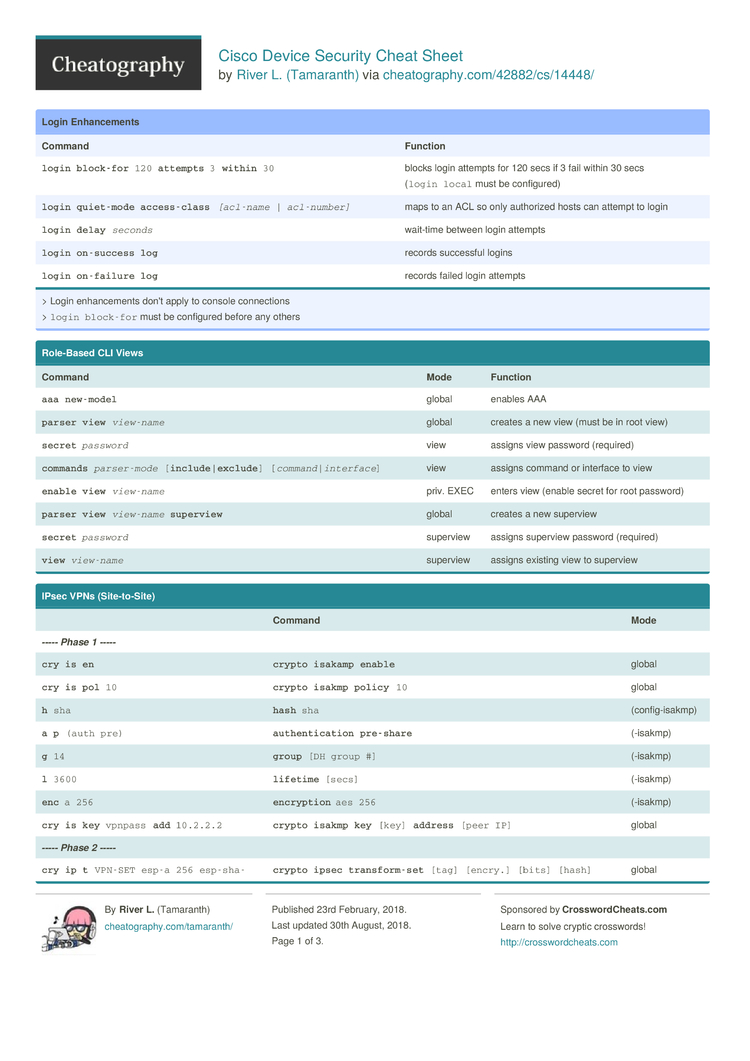
Cisco Device Security Cheat Sheet by Tamaranth - Download free from Cheatography - Cheatography.com: Cheat Sheets For Every Occasion
![Cisco Nexus 9000 Series NX-OS Security Configuration Guide, Release 7.x - Configuring AAA [Cisco Nexus 9000 Series Switches] - Cisco Cisco Nexus 9000 Series NX-OS Security Configuration Guide, Release 7.x - Configuring AAA [Cisco Nexus 9000 Series Switches] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/100001-200000/190001-200000/197001-198000/197006.eps/_jcr_content/renditions/197006.jpg)
Cisco Nexus 9000 Series NX-OS Security Configuration Guide, Release 7.x - Configuring AAA [Cisco Nexus 9000 Series Switches] - Cisco